Email trojan horse: application/html entity
We just discovered a new trick that is currently being used to slip malicious html files through email security solutions and, in some cases, through antivirus engines.
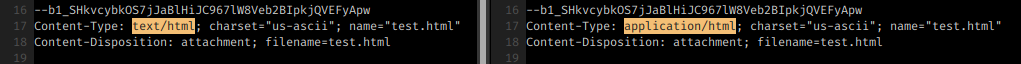
The trick is quite simple: declaring an email entity as “application/html” instead of “text/html”. “application/html” is an invalid type and this allows it to slip through some checks.
Background
Emails are composed of many “parts” called “entities”. Each entity has a content-type header that declares the type of it’s content (the textual or the html portion of the email, the images contained in the message, the attachments which can be of many different file formats). For example the html portion of the mail has content-type “text/html”, the text part is declared as “text/plain”, an image can be “image/png”, an attached office document can be “application/msword”, and so on. There is a list of valid types and “application/html” is not among those.
What happens if you declare an invalid content type? It depends. Email clients try to be helpful and tend to consider as valid the types they don’t know, but security solutions and antivirus engines may behave differently. They make specific security check that depend on the content and when faced with a content type they don’t know in some cases the end up ignoring or not analyzing properly the content of these entities. At least this is what happens with the entity type “application/html” that we tested.
Samples in the wild
The samples found in the wild are delivering html files that, as soon as they are opened, redirect to a malicious site (through a meta tag). These very small one-line html files are attached to malicious emails inside an entity of an invalid type “application/html” instead of the correct type “text/html”. All the email clients we tested (including the major webmail services) show these files as normal attachments but all the email security filters we tested (including those of the major wemail services) could not find malicious links contained in these html files if the entity was “application/html”. While they did detect them if contained in a normal “text/html” entity, they could not detect them if the entity type was changed to “application/html”. This trick is actively being used in the wild, this is why it is appropriate to go public with these findings.
Our testing
In order to assess how these entities are managed by email services and clients, we created two email samples with an html attachment containing a link to a malicious website. One of the samples has the entity type changed to “application/html” instead of the normal “text/html”. This is the only difference between the two samples.
The sample with the “application/html” entity was delivered as clean in the inbox of all the systems we tested (including the major email providers) while the very same email with the entity of type “text/html” was correctly classified as dangerous. Some checks are clearly missing when the entity type is “application/html”.
All it takes to create a “stealth” entity is to change the word “text” into the word “application” in the content-type declaration.
All the email clients (including major webmail services) allowed the user to open the html file contained in the “application/html” entity.
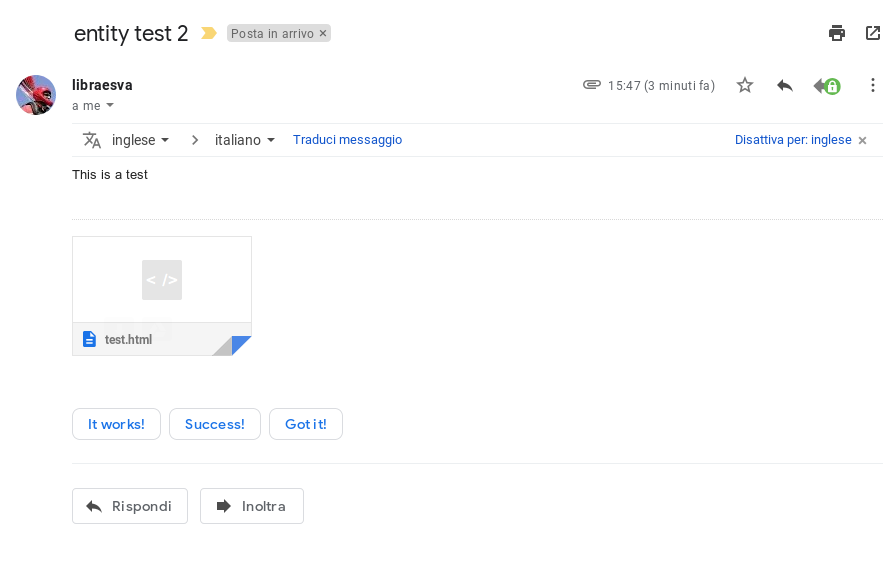
Here is the malicious html file inside an application/html entity sent to Gmail:
Clicking on the attachment, it is displayed and offered for clicking.
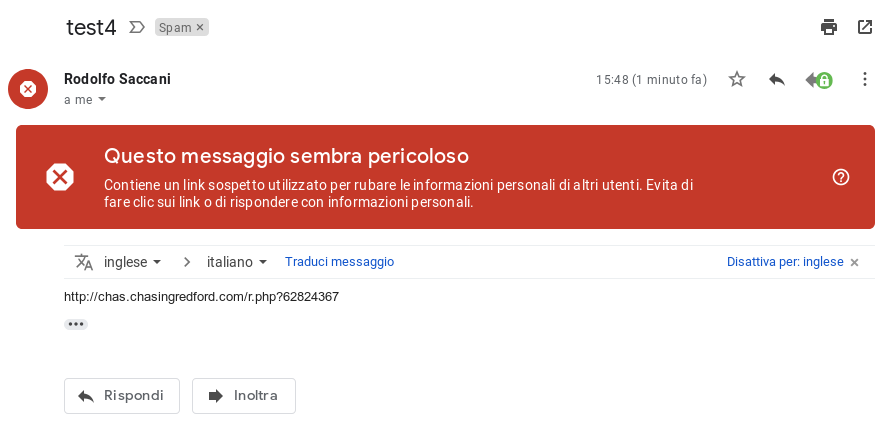
Here is the same malicious html file sento to Gmail in a normal text/html entity:
The text/html entity is properly analyzed and classified as dangerous, the application/html entity is not.
Tests with actual malware
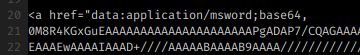
We performed a second test, by embedding a real sample of emotet in the html attachment (inside an href tag). With this sample the results varied: major email providers correctly detected the threat while some email filtering solutions didn’t.
The image above shows how we embedded emoted inside the html file.
These samples have been also tested with major and widely used antivirus engines: some of them did not inspect the “application/html” entity even if they could correctly detect the same sample in a “text/html” entity.
The target of this post is to raise awareness so there is no point in naming products here. We just show a test performed with an opensource antivirus engine.
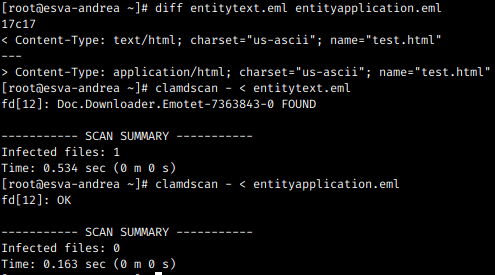
In the previous image we have two samples containing emotet embedded in the html file.
entitytext.eml had a normal “text/html” entity while entityapplication.eml had an entity of type “application/html”. The first command (diff entitytext.eml entityapplication.eml) shows that the only difference between the two emails is the word “text” replaced with “application” in the content-type declaration.
As you can see the antivirus detected emotet in the first sample and didn’t detect it in the second. This test used clamav but the same test with major commercial antivirus engines produced similar result.
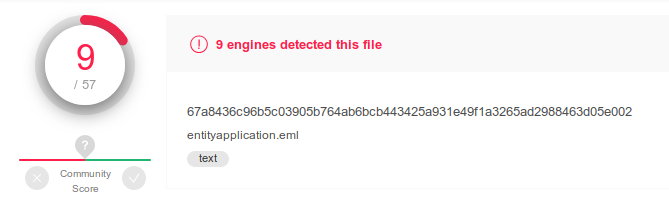
The sample entityapplication.eml uploaded on virustotal has been classified as malware by 9 engines on 57:
Conclusions
From an email security gateway point of view, blocking emails containing entities of type “application/html” is probably the wisest thing to do and this is what we are currently doing.
This is clearly an attempt to evade security inspection by pretending to be some kind of unkown application-specific data, inducing to perform only broad and general security checks (for example clamav does not decode base64-encoded data embedded in the href tag if declared as “application/html”) while, at the same time, inducing the email client to offer the file to the user as a normal html attachment.
An attempt to evade analysis is a strong signal about the malicious intention of the sender and should be penalized accordingly.
This threat has been added to our email security tester, a tool to assess the performance of emails security protections. This means that you can easily test, right now, whether you are protected or not from this and other common email threat vectors.