New DDE exploit variant currently not detected by any AV engine
DDE (Dynamic Data Exchange) is a very old and almost forgotten feature of Microsoft Office. Designed to automate the exchange of data between applications, it can be easily exploited to execute arbitrary code without any macro or other active content.
About one month ago, samples of office documents exploiting DDE to spread ransomware have been found in the wild. Security vendors quickly updated their products in order to detect and block such threats.
Unfortunately there are may ways to leverage DDE, some of which are quite elusive. Over the last few weeks new ways to exploit DDE eluding detection have been found and security vendors reacted with variable speed. Here, for example, is a sample of a .doc file that we posted on VirusTotal over three weeks ago. At that time no AV engine detected it, today, about one month later, less than one third of the engines detect it and some big names are among the ones that don’t.
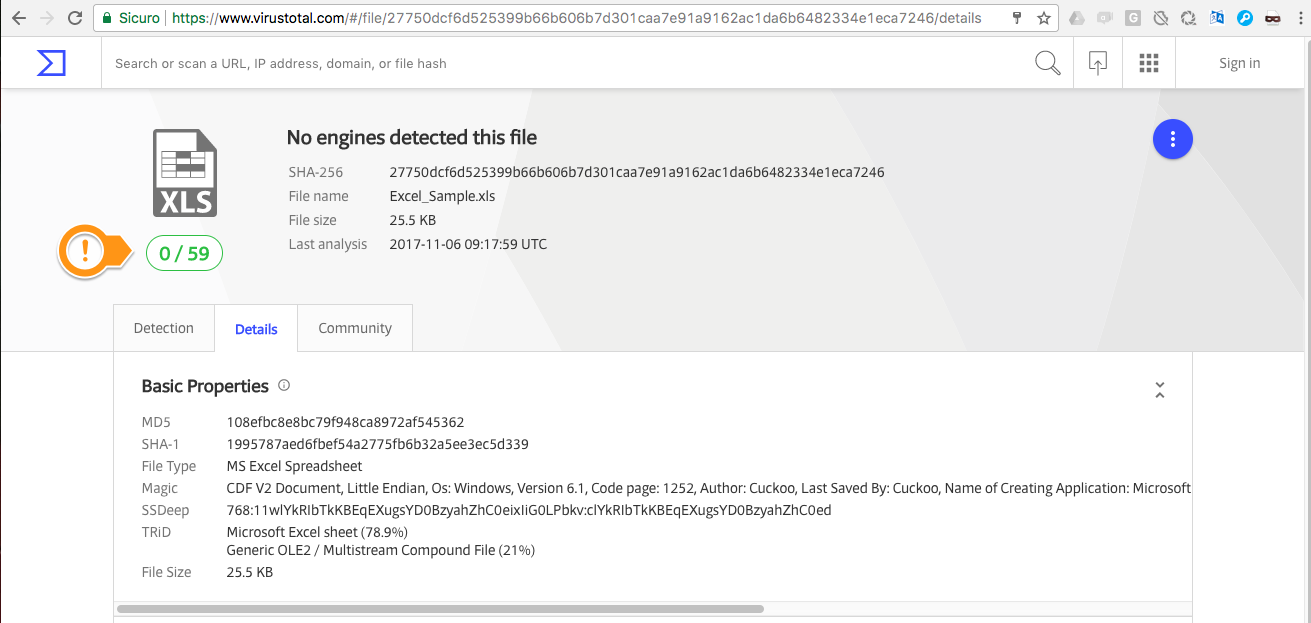
Now, we just created a new .xls sample that is currently detected by ZERO engines according to VirusTotal. This sample is harmless, it just demonstrates how to leverage DDE eluding detection: it uses DDE to launch powershell which in turn launches calc.exe. Once you manage to execute powershell you can let it dynamically download code from a remote website and execute it. This specific sample demonstrates how to exploit DDE without being detected, we’ve tested also harmful samples (using powershell to download and execute malicious code) with the same outcome.
As you can see from the screenshot above, the sample is currently undetected by all of the engines running on VirusTotal.
You can download the sample from VirusTotal, we also added this sample to our Email Security Tester, a service that sends you a few emails containing different types of threats in order to test your email security setup.
Rodolfo Saccani