Anti-phishing techniques and tools
There is a big illicit business out there and it’s driven by a simple old trick: deception.
Deception is at the base of many online black and gray activities, from click baiting to ransomware.
Pair deception with email and what you get is email phishing.
The target of e-mail phishing campaigns is inducing the victim to perform an action at the advantage of the attacker. It’s as simple as this.
In order to induce you to perform an action against your own interest, the attacker uses the following deception tools:
– a message that grabs your attention
– a sense of urgency
– a call-to-action
What if I tell you that your Apple account has been disabled and that you won’t be able to use your devices until you fix it?
What if you happen to know that money has just been withdrawn from your bank account? Maybe you should check immediately.
What if your mailbox quota has been exceeded and you won’t receive emails until you act?
Of course there are also incredible offers or you may be the winner of a great prize or maybe a young beautiful girl wants to know you.
I guess you’ve already experienced some of these messages, if not all of them.
So far for grabbing attention and transmitting a sense of urgency. What about the call-to-action?
The call-to-action, as usual, varies from clicking on a link to land on a site that drops it’s infective payload or asks you to enter personal information to opening an attachment.
It’s important to note, though, the difference between mass phishing and targeted phishing, also known as spearphishing.
Spearphishing is phishing targeted to a specific person, building a credible message based on knowledge gathered on social networking sites or other sources. Spearphihing is much more difficult to detect.
For the first Libra Esva Partner Event, in may 2016, I’ve done an interesting experiment. I’ve used the open source framework gophish to create a phishing campaign in order to assess, in practice, how effective such campaigns are.
Gophish is one among many tools that make it easy to create and phishing campaigns, it assists you in the whole process from the creation of the email template and landing page to the real time metrics and analytics. It’s a complete framework, it also acts as a web server to serve your phishing site.
Such phishing tools are particularly valuable for training your users not to fall for real phishing. You can run, for example, a phishing campaign on the employees of your company and then follow-up with a training session. The phishing campaign has both the advantage of measuring the effectiveness of your training over time and also to make the training more effective by attaching it to a real and direct experience.
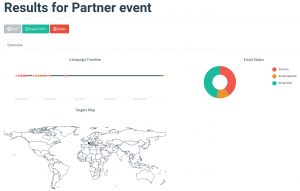
In my test, I created a fake LinkedIN contact request by grabbing the content of a real LinkedIN email. I also grabbed the content of a LinkedIN loging page to create my phishing landing page. Then I sent the phishing email to all the participants to the Partner Event.
The numbers suprised all of us.
We sent 44 emails, 24 of which have been opened. A respectable open rate of 54%.
18 “targets” clicked on the link and landed on our fake login page: 75% click-throug-rate.
We don’t know whether they attempted to enter their credentials or not because the page didn’t submit any data, it just informed the user of the phishing experiment when they pressed the “submit button”.
In the end, 40% of the “targets” ended up clicking on the link and this is all you need in order to get infected.
40% is a huge number considering that this was a very security-literate audience.
Remember: just clicking on a random link can get you infected. If you are not convinced about this just have a look at a the security fixes that Microsoft releases every second Tuesday of the month, search for the ones flagged as “remote code execution vulnerability”.
Phishing is a real danger because it is effective and very affordable. The good news is that with a reasonable effort you can use phishing to rise awareness among your users and make your training more effective.
How can an email security appliance help with phishing?
The standard spam fighting techniques are not sufficient for phishing. Phishing emails often closely resemble real emails from your bank, your service provider, you colleagues. They often come from legit end-user email accounts illicitly used with passwords coming from database breaches (don’t reuse your passwords, use a password manager) or from infected computers. Content analysis must rely on the detection of subtle differences.
Besides AV engines, filename and filetype policies, nested archive scanning, Libra ESVA provides “ESVA Labs” which is based on collaborative detection and expert analysis. Administrators and users of our appliances can report false positives and false negatives to our ESVA Labs. These reports are immediately delivered to us along with the internal analysis performed by ESVA and most of them are very pertinent. We don’t have to dig through hundreds of thousands of non-pertinent reports and we can quickly analyze them. Our analysis team updates and releases new detection rules usually within 30 minutes form the report, the new detection rules are automatically downloaded by all ESVA appliances every hour. Being quickly reactive is the key to fight phishing.
Rodolfo Saccani