When Ransomware Goes Beyond Revenue: Data Exfiltration Threats (and How to Protect Your Business)
Ransomware attacks have been lighting up the newswire for a few years now, and they aren’t going away anytime soon. According to TechCrunch, 2022 was the worst year on record for ransomware attacks, with increases of 80% year-over-year.
Ransomware is a type of malicious software that blocks access to a computer system until a specific amount of money is paid to the threat actors running the attack. These threat actors have been making easy money by exploiting the high value of cryptocurrencies and organizations’ lack of proper preparation and/or security guardrails. And, unfortunately, most of them get away with it.
Phishing – Threat Actors’ Favorite Tool for Ransomware
The most popular way to kickstart a ransomware attack? Phishing emails, according to Statista.com. With email an accessible channel to every employee within a company, it’s often hackers’ first choice in getting their ransomware messages through. Bad actors typically impersonate a company and trick their victims into either directly releasing account logins or clicking a malware-laced link. These links aren’t always easy to detect. Once they’re in, the malicious activity begins.
And the threat is only getting larger. The Anti-Phishing Working Group (APWG) reported that in the third quarter of 2022, it observed a total of 3 million phishing attacks, representing the worst quarter on record.
The Rise of Data Extortion
It’s true; ransomware is evolving to be more dangerous than ever before. With the expansion of data extortion via more sophisticated malware, threat actors aren’t only demanding money; they’re removing sensitive data from the systems they attack. This type of ransomware can come with a huge security price tag that can ruin a company’s reputation for many years to come.
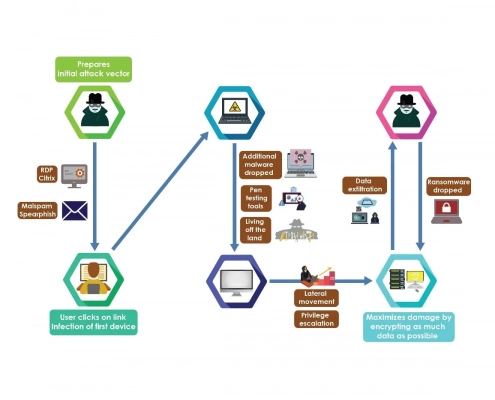
Unauthorized data exfiltration can be accomplished in a number of ways. For example, a threat actor could gain access to a compromised corporate email account to send and receive files outside of the network–the credentials for this access having been obtained during the initial ransomware attack. Then, they could use malware, open-source penetration testing tools, or other well-known techniques to move freely through the organization’s network. This access allows them to target the critical data they need to run their data extortion campaigns. Below is a typical infection process, as outlined by cisecurity.org.
Hackers are often selective about the data they steal, aiming for low-volume high-impact data first. Large-scale, “grab everything and go” data exfiltration is often noisier and easy to detect, so small-scale ransomware attacks use a gentler approach that often goes unnoticed until it’s too late. Threat actors may even choose to steal small amounts of data over multiple periods, magnifying the threat while minimizing their ability to get caught.
What’s a Security-Minded Business to Do?
Every company, no matter its size, should be concerned about ransomware, particularly with data extortion on the rise. Here are some steps businesses can take to ensure they are both protected and prepared for an attack.
-
-
Enable Email Filtering
With phishing emails the first fault line for many ransomware attacks, setting up content rules for your organization’s emails is the first step. Partnering with a provider like Libraesva ensures your email security, including filtering, is nearly impenetrable.
-
Invest in AI Threat Detection & Response Technology
AI technology is on the rise, and with it, comes threats from AI-powered bad actors. Look for solutions that consider Machine Learning, Computer Vision, and Natural Language Processing to help detect malicious activity. Then, implement solutions that provide continual scanning and automatic remediation to ensure your organization has ongoing protection.
-
Encourage User Awareness Training
Human error continues to be the number one driver of successful online attacks. According to IBM and the Ponemon Institute, 21% of data breaches globally in 2021 were caused by human error. Consider regular automated training and ongoing threat detection exercises to keep employees vigilant.
-
Consider Blocking 3rd-Party File-Sharing Services
If your organization can find other solutions, consider blocking third-party file-sharing sites such as Dropbox. These sites offer an easy way to exfiltrate moderate volumes of data easily.
-
Build an Incident Response & Communication Plan
Create and maintain a cyber incident response plan with response and notification procedures and other communications plans so that you are prepared in the event of an attack.
-
Implement DMARC Policy & Verification
DMARC beefs up your security by expanding on the Sender Policy Framework and Domain Keys Identified Mail protocols through the addition of policy enforcement and a reporting function for senders and receivers.
-
Vet MSPs
MSPs are often a “weak link” in organizations’ security policies. Consider the risk management and cyber hygiene practices of all 3rd parties your company uses.
-
Adopt Zero Trust Security Policies
By adopting Zero Trust security, you make it harder for hackers to harm your network after achieving initial access through the use of technologies like multi-factor authentication (MFA), access controls, and network segmentation.
-
Implement Password Protection Policies
Ensure employees are using secure passwords via security training, password protocols, regular refreshes, password managers, and other related methods.
-
Consider Threat Detection Tools & Maintain Ongoing Logs
Analyze tactics and tools to detect threats from the start, such as an intrusion detection system (IDS), an intrusion prevention system (IPS), or an Endpoint Detection and Response (EDR) solution. Then, analyze baseline network activity over time to determine behavioral patterns. Determining what constitutes normal activity is a major step in detecting malicious network activity.
-