The global email security market was valued at approximately $5.23 billion in 2025, with continued growth driven by increasing cyber threats and the adoption of AI-enabled security tools and detection.
These AI-driven solutions have significantly improved the security posture of many organizations, introducing capabilities such as advanced social engineering warnings, improved phishing detection, and more accurate malware alerts. But as AI usage continues to accelerate, it’s increasingly important to ask a foundational question: where does sensitive email data reside during analysis—and under whose control?
As we enter 2026, growing geopolitical uncertainty, increased scrutiny of supply-chain risk, and heightened awareness of third-party dependencies have brought data sovereignty into sharper focus across Europe and beyond.
Even in regions without strict regulatory mandates, organizations are becoming more cautious about business communications being processed outside their organizational or regional control.
Email security is a particular area of concern. Emails often contain financial data, personal information, internal strategy, and other highly sensitive content. Because of this, it’s critical to understand how that data is analyzed, how long it is retained, and where processing takes place.
Cloud-Based Email Security: The Pros and the Tradeoffs
Many modern email security platforms rely on large, resource-intensive AI models to operate effectively. In some architectures, this can involve sending email content to external cloud services or general-purpose LLMs for inspection and classification.
Cloud-based approaches offer clear advantages in scalability and speed of innovation. However, they can also introduce tradeoffs, especially when email data is transferred beyond tightly controlled processing environments.
Moving sensitive communications outside a defined security boundary can increase dependency on third parties, expand the attack surface, and reduce transparency around how data is accessed, processed, or retained.
For some organizations, this raises regulatory or compliance concerns. For others, there’s a concern about loss of control and visibility over critical business data.

Controlled, Purpose-Built AI by Design
Privacy-first email security starts at the architectural level. Purpose-built AI operating within tightly controlled, regionally bound environments limits data access, reduces unnecessary data movement, and avoids reliance on general-purpose cloud LLMs or opaque processing chains.
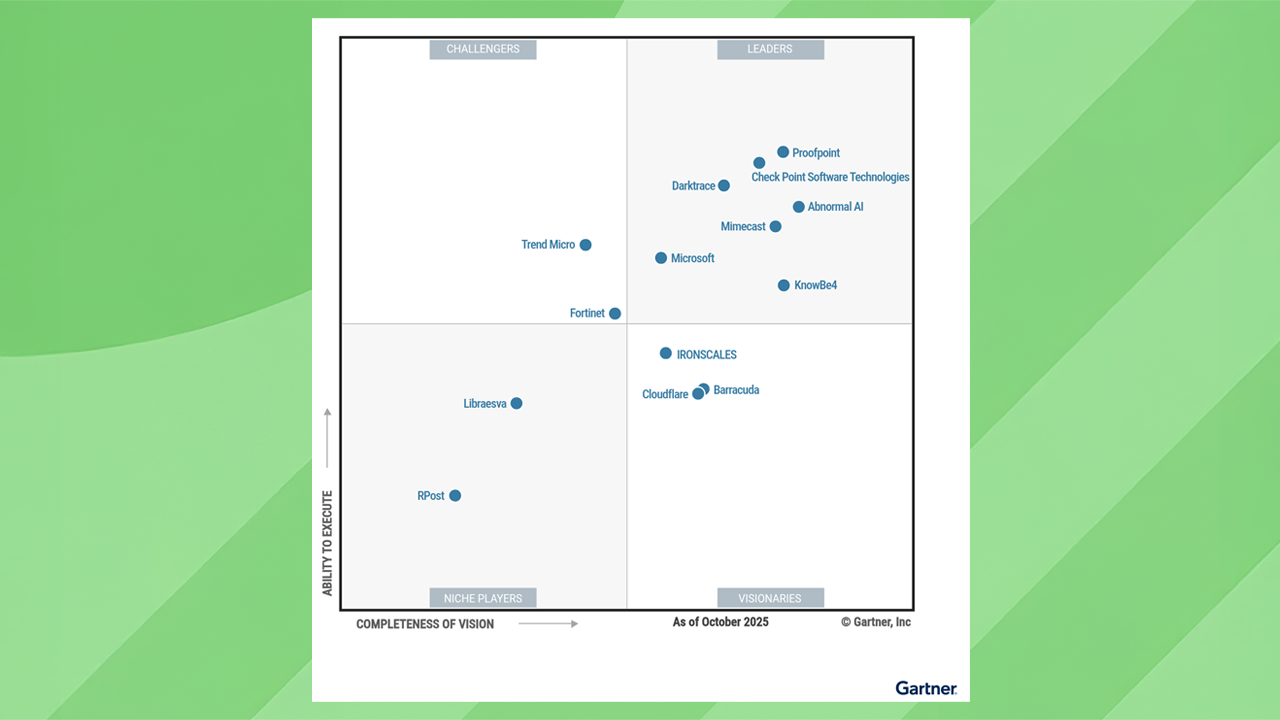
Libraesva’s email security platform is built around this principle, with context-aware, privacy-first AI purpose-built for email threat detection. Libraesva analyzes intent and meaning without offloading message content to generic cloud-based AI services. Semantic and adaptive trust engines operate within controlled environments, with strict limits on data access and retention.
With Libraesva, deep inspection and sandboxing are performed locally within the customer environment, organizations can minimize unnecessary data movement while gaining greater control over their communications and regulatory posture. Deterministic, explainable analysis helps security teams understand why a message was blocked or allowed.

Compliance as an Outcome, not a Retrofit
When privacy-first principles are embedded at an architectural level, compliance becomes easier to manage by design. Requirements around data handling, residency, and access are addressed in the email security architecture by design, rather than relying on compensating controls or contractual assurances after the fact.
This is increasingly important as regulatory expectations evolve and enforcement tightens. But even outside regulated industries and environments organizations benefit from architectures that reduce unnecessary data exposure and lower long-term operational risk.
A Global Shift in Expectations
While European regulations have helped elevate data sovereignty discussions, concerns about data exposure, cloud dependency, and third-party risk are applicable across the globe.
It’s time for IT and security leaders to ask fundamental questions about their security stack:
- Which entities/services process our data?
- Where does it go?
- And what assumptions are we making in exchange for convenience?
The answers to these questions are becoming harder to ignore.
As AI continues to reshape the threat landscape, effective security is no longer just about detection accuracy. It’s about control, transparency, and ensuring sensitive data remains governed by the organization that owns it.
Are you evaluating your email security architecture?
See why security leaders are prioritizing control, transparency, and purpose-built AI with Libraesva.