Malware evades Sandbox, can security solutions catch up with it?
Yesterday evening, I was reading some security feeds and I came across a great blog article posted by @a_de_pasquale heading “New password Protected Macro Malware evades Sandbox and Infects the victims with Ursnif Malware!!”
I do not want to annoy you with the malware specific architecture and working, if you wish you can read the full story at following link: https://cysinfo.com/new-password-protected-macro-malware-evades-sandbox-infects-victims-ursnif-malware/.
Three magic words captured my attention: “Malware evades Sandbox”!
The article deepens into a sandboxing analisys and shows how opening the document with Microsoft Word in a fully sandboxed virtual machine and observing it’s behaviaour cannot detect anything suspicious, considering the document safe while is not!
At Libraesva we declare that our QuickSand Protection technology is “Virtually immune to sandbox evasion techniques!”.
The principle of everything we do at Libraesva starts from real life experience and we stand for our commitment in delivering real protection and not pure marketing stuff !
Is that true ? Or is our brand new QuickSand Protection Technology vulnerable to this piece of Malware, that evades all the security controls to infect the targeted machines?
Passion in our work drives us to be “always on” and I was so keen to send this kind of stuff through our appliance and check the QuickSand Protection we offer, that I started searching for the original document with my Ipad.
Yesterday evening I promised myself to spare some family time and I left my notebook in the office, at least that was the intention.
Still, the temptation was too strong and with my iPad I was only able to get the malware samples hashes posted on Paylod Security (https://www.hybrid-analysis.com) without being able to download and uncompress the sample itself.
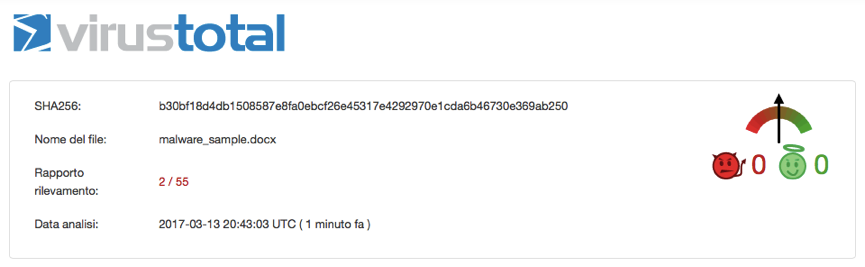
So I took my daughter’s macbook , I registered at Payload Security to download the malware, I have extracted it, renamed the file to malware_sample.docx and fired up my Gmail account to send a new email to my business email, protected with Libra Esva. Note that the malware has been analyzed for the first time on March 2nd 2017 by Payload Security, so I would expected some kind of security warning.
Surprisingly Gmail allowed to attach the malware sample without any warning, all good. I sent the email and after 10 seconds I got it in my business inbox.
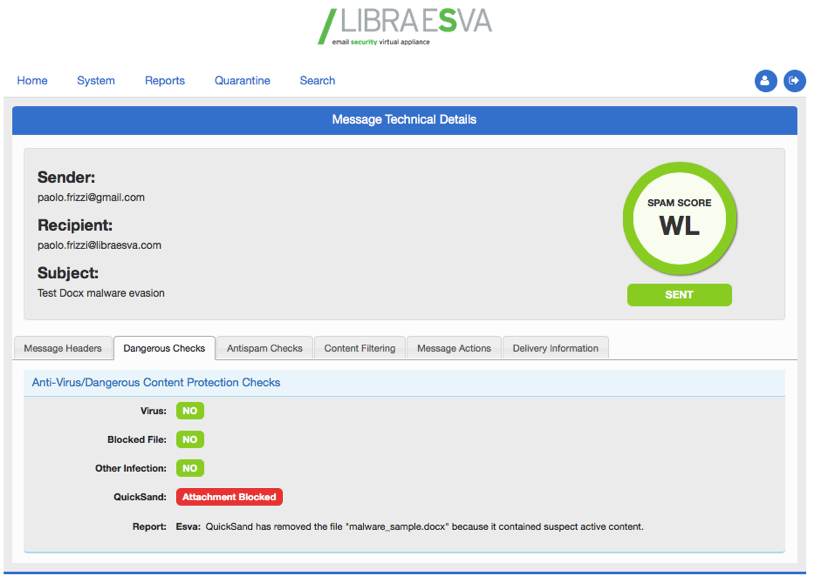
What’s happened? The email came through but the original attachment (the malware sample) has been replaced by our QuickSand Protection warning: “QuickSand has removed the file “malware_sample.docx” because it contained suspect active content.”
To cross check the industry standards, I then submitted the sample to Virustotal: this kind of malware still slips through 53 out of 55 AV Engines on VirusTotal after 12 days since it’s first submission!
It seems the industry giants are still catching up with this kind of infections.
At that point I was pleasantly surprised about what we did and with a full sense of pride of our simple technology I started writing this article focusing on some questions about cyber-security :
- do we need complicated and expensive technology to stop these threats?
- Is the root problem due to a technological factor or to a social approach?
I trust we all agree on the latter, as the ransomware business relies on people actions. And certainly we do not need to have fancy screenshots of a virtual environment running the malware without detecting it, just to have a nice report that complacency. Without considering the resources and time needed to run it, introducing delays in people productivity and mining their privacy if sending the document to a cloud sandbox for the analysis. Libra Esva QuickSand Protection runs entirely at the gateway and does in deep source code analysis, it takes a few seconds and it is very effective!
Again:
- Can the technology help educating people?
Sure it can! But what if we deliver a common sense of protection with marketing slogans that do not reflect the real like scenarios?
Why most security vendors do not disclosure their deductive calculations in classifying contents as safe or dangerous? Is there anything to hide? Why everything in cyber-security is so complicated?
I believe that the correct approach is definitively based on transparency: explain people your approach, tell them which checks you do, don’t be afraid to detail why you missed a malware or a malicious email. Do not build a wall in between customers and support with complicated policies that discourage customers from asking.
And finally do not let the fireworks of a fancy dashboard drive your development in the name of marketing. And do not stand with sentences that are simply stupid: the end of ransomware! We block 100% of known malware! And more… Be pragmatic, customers are not stupid.
We need that kind of approach in Cyber-security!
Lecco, March, 14th 2017
Eng. Paolo Frizzi
