Outlook comments abused to deliver malware
It’s no secret that Microsoft’s Office features are so nice and powerful that attract the attention of the bad guys, always trying new ways to get into your data.
Getting an email to look good with Microsoft Outlook, with it’s terrible CSS support, can be difficult at the best of times, unless you take advantage of Microsoft’s Conditional Tags!
All you need is to insert a special HTML comment that Microsoft’s client can decode and execute:
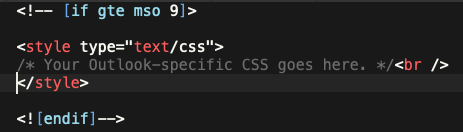
This code will simply be ignored by other email clients, as it’s a comment by definition. Simple and powerful!
So powerful that the bad guys already exploited this feature, coding the malware link into HTML comments that are ignored by many email security gateways as well, so passing through the filters.
Let’s see an example to make it clear how it works: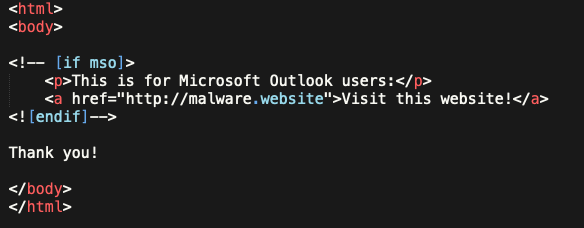
In the above example the link has been defined inside an HTML comment. Should be accordingly ignored by all HTML rendering engines, but as said Microsoft Outlook client (all Windows versions) is an exception.
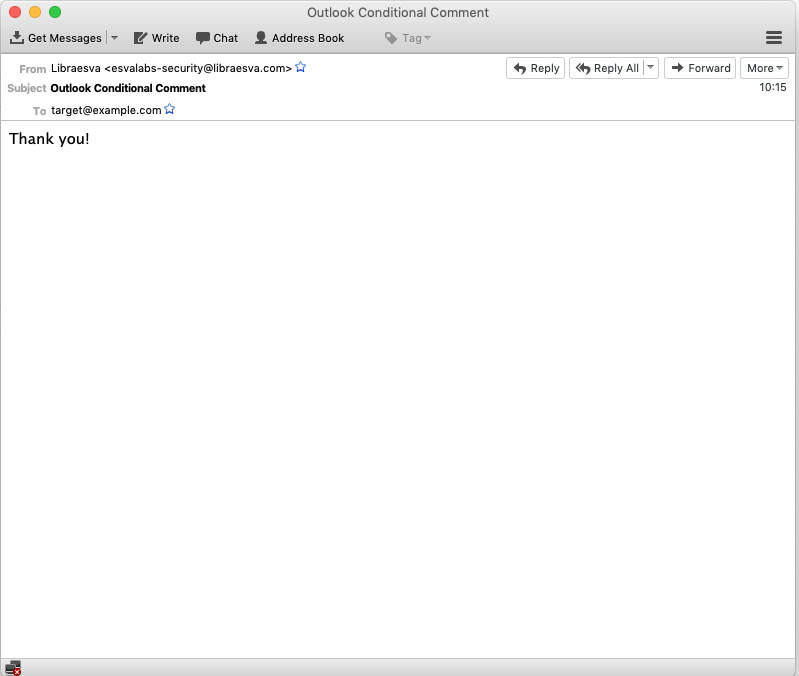
This is how the email is visualized on a generic email client (Mozilla Thunderbird):
And this is how the email is rendered to a Microsoft Outlook user:
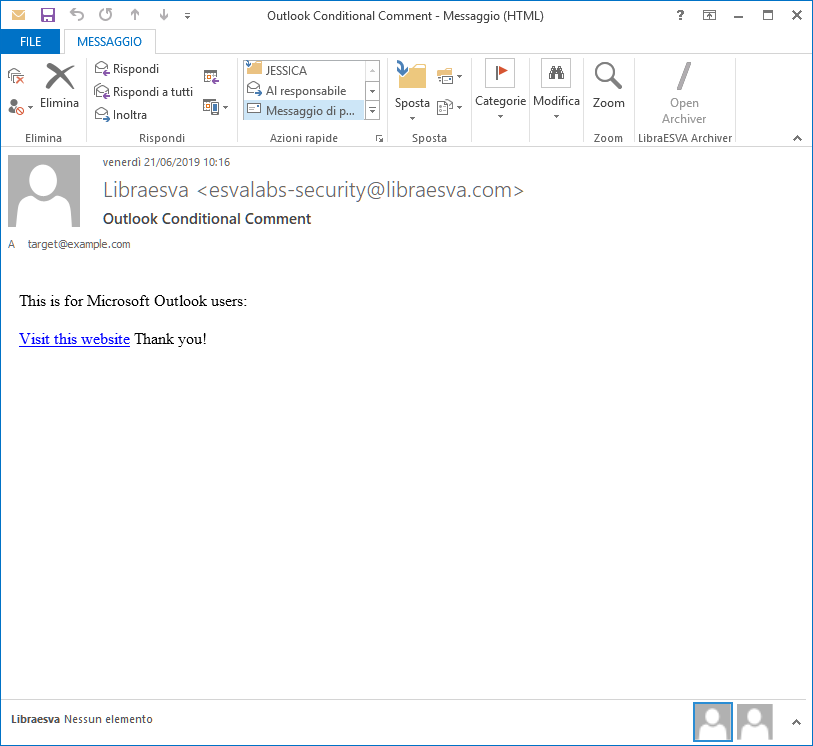
The above link could be used to drive the user to a phishing or malware website!
This is a real life example of what we see in our labs on a daily basis, malware guys are always trying different technics to evade detection.
How to be protected against this attack?
A good Email Security Gateway should be able to disarm HTML comments in email!
Unsure if you are protected?
You can safely and easily run our Libraesva Email Security Test that will simulate most common email threats, including this one!
