Phishing campaign uses Google reCAPTCHA to avoid Sandbox detection
Recent email phishing campaigns are using Google reCAPTCHA as part of their efforts to bypass click-time protection sandboxing, requiring user interaction before delivering the actual contents of the phishing page.
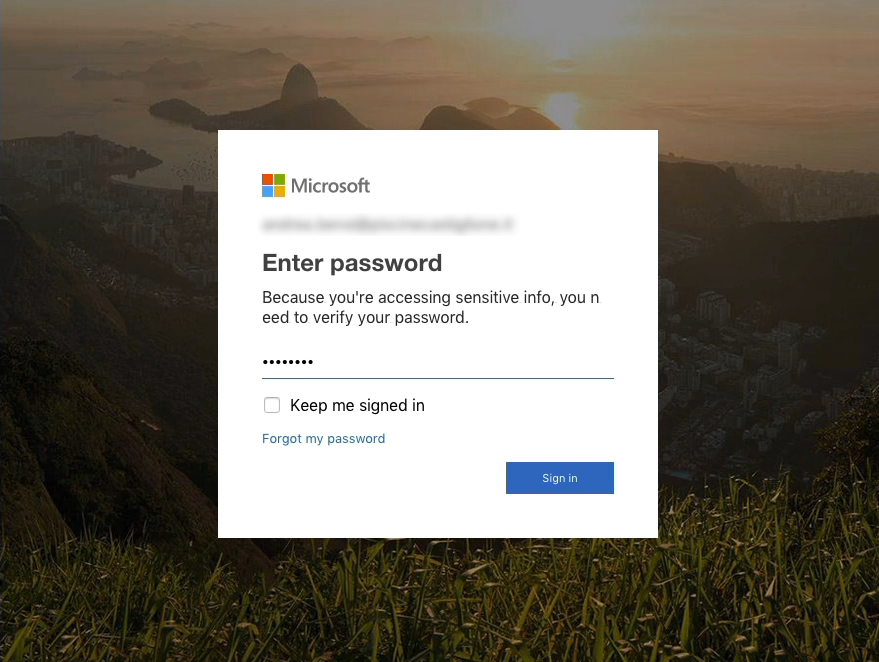
We have seen two different instances of such campaigns, both are targeting Office 365 users in order to collect their credentials. Implementation details suggest that the two campaigns are not coming from the same actors.
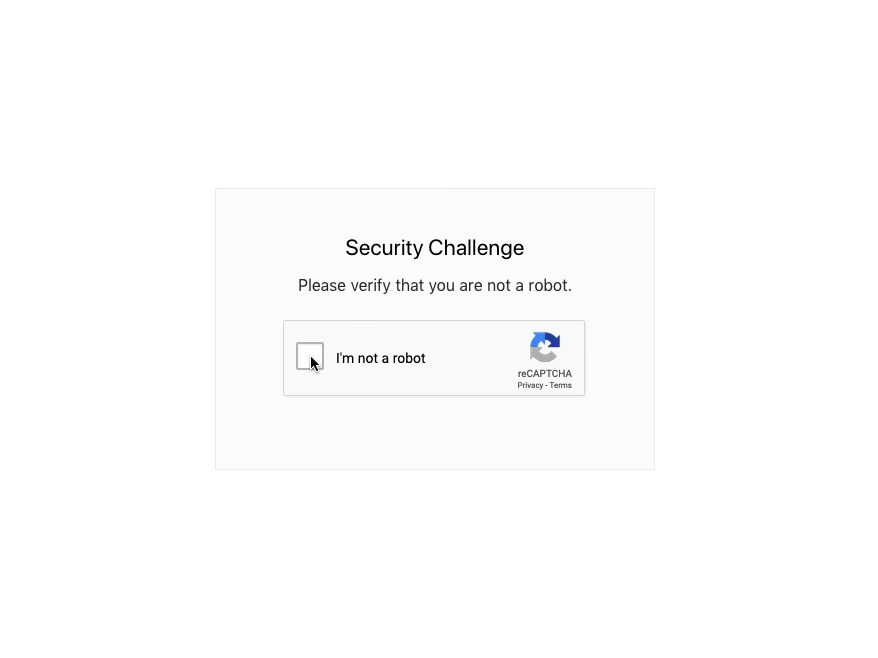
In both instances, as soon as the user clicks on the link contained in the email and the browser lands on the page, a Google reCAPTCHA is displayed in an otherwise empty page:
This is intended to act as a barrier for automated scanning services, letting only humans go through this first step.
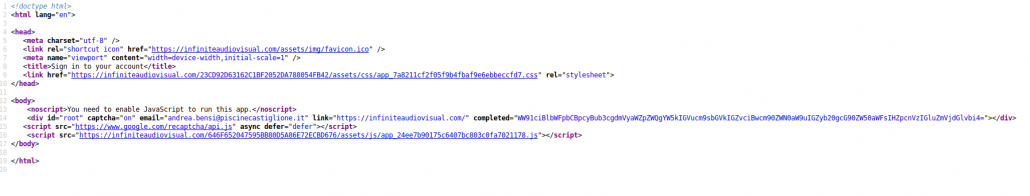
The phishing web application is built using React, a widely used javascript framework. The level of skills required is well above the average for such phishing campaigns.
After the reCAPTCHA has successfully confirmed that the visit comes from a human, then the real phishing page is displayed:
Phishing campaigns keep improving. Evading the inspection from bots increases the longevity of the phishing site by delaying the moment the website is blacklisted and browsers start displaying red warnings to users visiting it. In this case the phishing site is still online and not blacklisted after more than 5 days at the following domain infiniteaudiovisual[.]com.
Here is a video of the whole process:
URL sandboxing services like Libraesva URLSand, by visiting the page at click-time, can afford to make deeper checks on the contents of the website and on it’s behavior in reaction to real clicks originated from real phishing emails.
Besides searching for phishing toolkits and patterns, besides semantic analysis and heuristics, besides reputation checks and machine learning, our URLSand actively seeks for evasion and obfuscation attempts.
Evading detection is crucial but it provides useful signals to the expert analysis of specialized automated security systems which are continuously kept up to date by our Esvalabs team.
This is the approach that allows our URLSand to block this and similar threats.