Targeted attacks through mobileconfig attachments
We spotted an instance of what appears to be a targeted attack through a phishing email delivering a .mobileconfig file. This is a file format used to deliver configurations to iphones.
The attack originates from domain that appears to have been created just for this purpose.
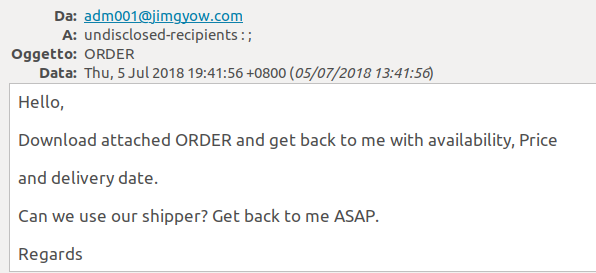
This is how the email appears to the recipient:
The attachment of course is not an order but the mobileconfig file.
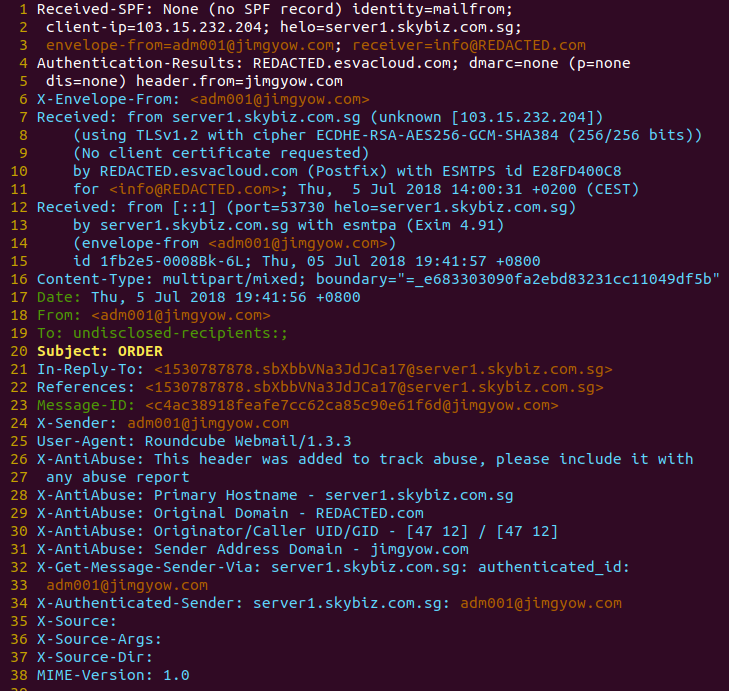
Here are the email source headers of this email coming from the domain jimgyow.com, I’ve redacted the information about the recipient:
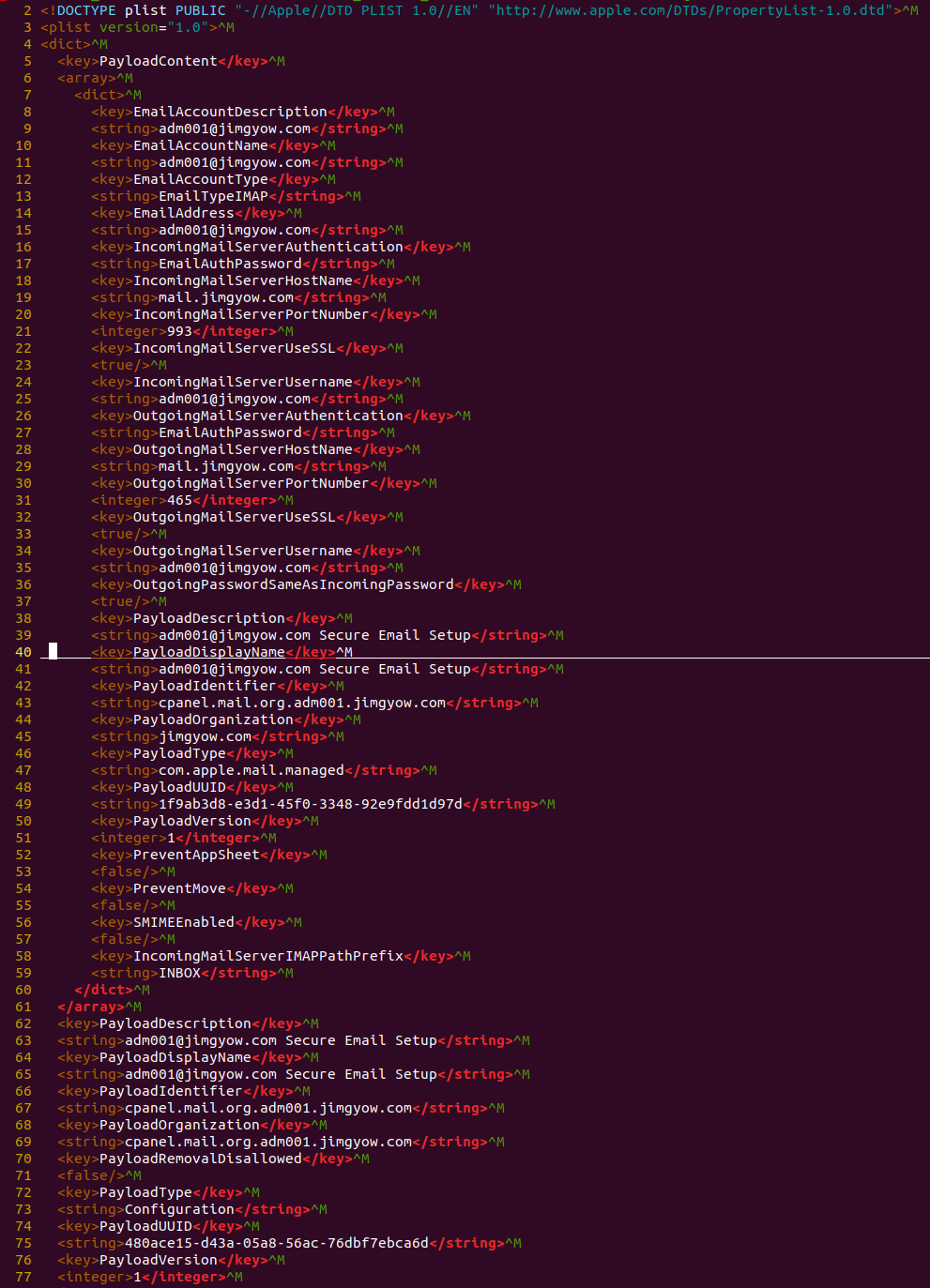
The attachment is a file named [email protected] whose content is displayed in the following image:
Once opened, the file will automatically configure, on the victim’s iphone, a new email account for the address [email protected]. The configuration file does not provide the password, which will then be prompted to the user and submitted to the mail server controlled by the attacker.
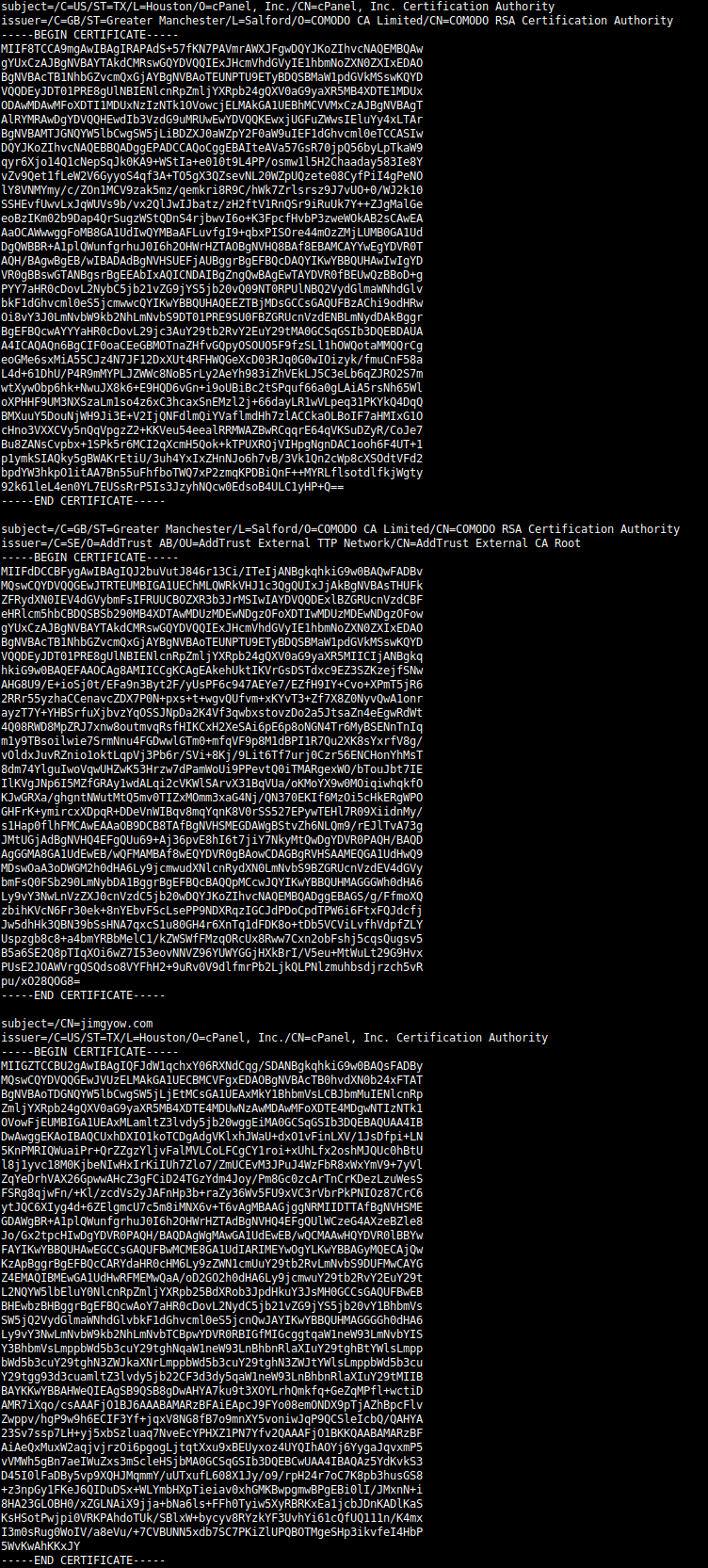
The configuration file is signed with a valid certificate issued to jimgyow.com:
If you have information about other uses of this attack vector, we’d be happy to hear from you. Just use the “contact us” form on this website.
Rodolfo Saccani, security R&D manager at Libra Esva