Whaling, Business Email Compromise and CEO Fraud
Whaling, Business Email Compromise and CEO Fraud
You’re probably familiar with Whaling and Phishing attacks by now, the simple fact that you either are a security professional or work in the cyber sector probably means you are actively facing this threat day in, day out. We at Libraesva fancy shedding a little light as to what makes whaling… whaling.
Let’s start with why, why are these attacks happening, well the first reason is because they are pretty easy to do, simply spoofing the email address is one way of attack, impersonation can be done using a wide range of techniques both technical and social. With name similarities, domain similarities, social engineering and so on. This type of attack can be devastating for organizations and quite lucrative for the attacker with little to no effort needed on the bad guy’s part.
The attack usually starts with a brief email pretending to come from a C-level executive. “Are you in the office?” is a typical approach. If the victim replies, then the attacker knows that his email slipped through the defenses and that the victim didn’t spot the scam. The attack can now proceed toward the final target: a wire transfer or divulging sensitive data.
From an email security perspective, this kind of attack is particularly difficult to block because the emails do not have links or attachments, they are brief, the messages use a type of language that is common in business emails.
The number of these attacks is quickly rising, and it is reaching companies of all sizes. It is also being semi-automated, at least for the initial email approach. Huge losses have been caused by these types of targeted attacks.
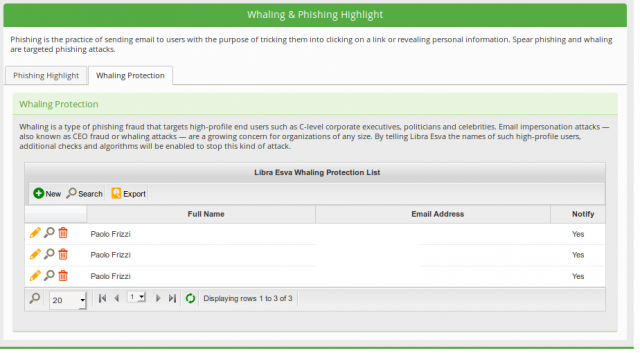
Libraesva designed a specific engine in order to intercept these attacks. The required configuration is minimal: the names and the legit email addresses of the company executives. Email addresses on external email providers are supported if the emails are DKIM-signed in order to protect against spoofing. Knowing the legitimate names and email addresses of the C-level executives, the engine can perform deep content analysis that would not be feasible to be performed on all messages.