What is the Libraesva QuickSand Sandbox
The Libraesva Quicksand Sandbox is a security service that protects the Libraesva customers from malicious active content in Microsoft Office and PDF Files.
- What is active content?
Active content is any executable code embedded in a document, like macros, JavaScript code and ActiveX applications.
Quicksand runs on our Email Security Gateway, for free, meaning that files never leave the gateway.
As the name suggests, the sandbox is very quick and efficient, the attachments are analysed at the same time as the generic email analysis with no delays and isn’t vulnerable to traditional sandbox evasion techniques.
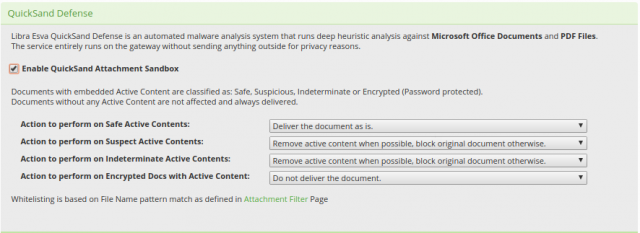
Quicksand identifies active content inside documents and classifies it based on the behaviour, these categories of behaviour are categorised as:
- Safe: Active content is present and it does not perform any critical operation in respect to security
- Suspicious: Potentially critical actions are performed by the active content like downloading data from the internet, launching programs, performing actions on the file system and so on
- Indeterminate: Active content is present but for technical reasons it’s behaviour cannot be categorised with enough accuracy
- Encrypted: The document is encrypted and therefore it is not possible to tell whether there is active content inside
For each of these categories, you can choose what to do with the file:
- Deliver: deliver the file as is
- Sanitize and deliver: disarm the active content and deliver the disarmed document
- Block: do not deliver the file, it will be removed from the email
Not all of the actions are available for all of the categories, for safety reasons. You can also define fallback actions in case the document cannot be sanitised for technical reasons.
Hopefully this blog post helped you understand a bit more behind our key product feature QuickSand. Please contact us if you need any additional information, or follow this URL here
Which will showcase the feature in a bit more technical depth.